Featured News
Nmap 7.00 Released
The Nmap Project is pleased to announce the immediate, free availability of the Nmap Security Scanner version 7.00 from https://nmap.org/. It is the product of three and a half years of work, nearly 3200 code commits, and more than a dozen point releases since the big Nmap 6 release in May 2012. Nmap turned 18 years old in September this year and celebrates its birthday with 167 new NSE scripts, expanded IPv6 support, world-class SSL/TLS analysis, and more user-requested features than ever. We recommend that all current users upgrade. The top 6 improvements in Nmap 6 are:
- Major Nmap Scripting Engine expansion, including 167 new NSE scripts
- Mature IPv6 support
- Infrastructure upgrades, including a bug tracker
- Faster scans
- Enhancements to SSL/TLS scanning
- Extreme portability
For full details, see the release notes or skip straight to the download page.
Rebooting the Full Disclosure Mailing List
Much of the security community has missed the Full Disclosure Mailing List since it abruptly shut down on March 19, so we've decided to reboot it for a fresh start! You can subscribe to the new list here.
Icons of the Web
![]() The Nmap Project is pleased to release our new and improved Icons of the Web project! We scanned the Internet's top million web sites and created an interactive 5-gigapixel collage of the results. You can explore it with our online viewer including pan/zoom and search capabilities to find your favorite sites.
The Nmap Project is pleased to release our new and improved Icons of the Web project! We scanned the Internet's top million web sites and created an interactive 5-gigapixel collage of the results. You can explore it with our online viewer including pan/zoom and search capabilities to find your favorite sites.
Nmap 6.40 Released
Nmap 6.40 is now available with with 14 new NSE scripts and hundreds of new OS and version detection signatures. It also includes great new features such as Lua integration for scripting Ncat, and initial support for NSE and version scanning through a chain of proxies, improved target specification. Of course there are many performance enhancements and bug fixes too!You can read the full details or download it free here.
Nmap 6.25 Released
We're proud to release Nmap 6.25 with hundreds of improvements, including 85 new Nmap Scripting Engine scripts, Nearly 1,000 new fingerprints for OS detection and service/application version detection, and Performance enhancements such as the new kqueue and poll I/O engines.You can read the full details or download it free here.
Nmap 6.00 Released
The Nmap Project is pleased to announce the immediate, free availability of the Nmap Security Scanner version 6.00 from https://nmap.org/. It is the product of almost three years of work, 3,924 code commits, and more than a dozen point releases since the big Nmap 5 release in July 2009. We recommend that all current users upgrade. The top 6 improvements in Nmap 6 are:
- Major Nmap Scripting Engine enhancements, including 289 new NSE scripts
- New web scanning capabilities
- Full IPv6 support,
- A new tool named Nping for packet generation and response analysis
- More capable Zenmap GUI and results viewer
- Faster scans
For full details, see the release notes or skip straight to the download page.
SecTools.Org Relaunched
3,000 people participated in the latest top security tools survey and we have relaunched SecTools.Org with the new data! We have also dramatically improved the site—it now allows user ratings and reviews, tracks release dates, offers searching and sorting, and allows you to suggest your own favorite tools. Are you familiar with all of the 49 new tools in this edition?
Nmap 5.30BETA1 Released With 37 New Scripts, Nping, and New Apple Vulnerability
We're proud to release Nmap 5.30BETA1 with about 100 significant improvements, including:
- 37 new NSE Scripts, covering SNMP, SSL, Postgress, MySQL, HTTP, LDAP, NFS, DB2, AFS, and much more.
- Nmap developer Patrik Karlsson found a major remote vulnerability in Mac OS X, which allows access to files in the parent directory of an AFS share. He wrote a detection/exploitation NSE script, which you'll find in this release.
- An alpha test version of our Nping packet generation utility.
News reports: ITWire, SANS Diary (brief), PenTestIT (brief)
Nmap 5.20 Released
 We're happy to release Nmap 5.20, offering 150+ significant improvements over 5.00, including:
We're happy to release Nmap 5.20, offering 150+ significant improvements over 5.00, including:
- 31 new NSE Scripts
- enhanced performance and reduced memory consumption
- protocol-specific payloads for more effective UDP scanning
- a completely rewritten traceroute engine
- massive OS and version detection DB updates (10,000+ signatures)
- Zenmap host filter mode shows just the hosts you're interested in.
For a more detailed list of changes, see the release notes. Source packages as well as binary installers for Linux, Windows, and Mac OS X are all available from the Nmap download page.
Nmap 5.00 Released!
 After more than 18 months of work since the 4.50 release, Insecure.Org is pleased to announce the immediate, free
availability of the Nmap Security Scanner version 5.00 from https://nmap.org. With nearly 600 significant changes, we consider this the most important Nmap release since 1997 and we recommend that all current users upgrade!
After more than 18 months of work since the 4.50 release, Insecure.Org is pleased to announce the immediate, free
availability of the Nmap Security Scanner version 5.00 from https://nmap.org. With nearly 600 significant changes, we consider this the most important Nmap release since 1997 and we recommend that all current users upgrade!
The release notes provide the top 5 improvements in Nmap 5 as well as example runs and screen shots. The change details section includes improvements to the Nmap Scripting Engine, Zenmap GUI and Results Viewer, the new Ncat tool, the new Ndiff scan comparison tool, performance improvements, the new Nmap book, and much more!
Source packages as well as binary installers for Linux, Windows, and Mac OS X are all available from the Nmap download page.
Update: We've gotten some great press from ITWire, Slashdot, SecurityFocus, LoveMyTool, Reddit, Linux Weekly News, InternetNews.Com, Twitter, and dozens more.
Nmap Network Scanning
After years of effort, we are delighted to release Nmap Network Scanning: The Official Nmap Project Guide to Network Discovery and Security Scanning!
From explaining port scanning basics for novices to detailing low-level packet crafting methods used by advanced hackers, this book by Nmap's original author suits all levels of security and networking professionals. The reference guide documents every Nmap feature and option, while the remainder demonstrates how to apply them to quickly solve real-world tasks. Examples and diagrams show actual communication on the wire. Topics include subverting firewalls and intrusion detection systems, optimizing Nmap performance, and automating common networking tasks with the Nmap Scripting Engine.
Visit the NNS web site for a detailed summary, reviews, and sample chapters, or buy it now from Amazon.
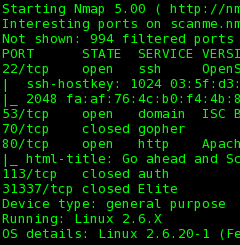
Nmap 4.85BETA7 Released to Scan for Conficker Worm
The Conficker worm is receiving a lot of attention because of its vast scale (millions of machines infected) and advanced update mechanisms. Conficker isn't the end of the Internet (despite some of that hype), but it is a huge nuisance we can all help to clean up.
Thanks to excellent research by Tillmann Werner and Felix Leder
of The Honeynet Project and
implementation work by Ron Bowes, David Fifield, Brandon Enright, and
Fyodor, we've rolled out a new Nmap release which can remotely scan
for and detect infected machines. Nmap 4.85BETA7 is now available
from the download page,
including official binaries for Windows and Mac OS X. To scan for
Conficker, use a command such as:
nmap -PN -T4 -p139,445 -n -v --script smb-check-vulns,smb-os-discovery --script-args safe=1 [targetnetworks]
You will only see Conficker-related output if either port 139 or 445 are open on a host. A clean machine reports at the bottom: “Conficker: Likely CLEAN”, while likely infected machines say: “Conficker: Likely INFECTED”. For more advice, see this nmap-dev post by Brandon Enright.
While Conficker gets all the attention, 4.85BETA7 also has many other great improvements.
Update: Changed version from 4.85BETA5 (first to detect Conficker) to 4.85BETA7, which includes further Conficker detection improvements, among other changes.
More information is available from: The Register, Slashdot, Washington Post, SecurityFocus, CNet, SC Magazine, ComputerWorld, SkullSecurity (Ron Bowes), Beta News, PC World, eWeek, CRN.com, TechNewsWorld, DarkReading, ComputerWeekly, PC Magazine, Threat Post, ZDNet.
Nmap 4.75 Released
We are pleased to release Nmap 4.75, with almost 100 significant improvements since version 4.68. Key Nmap 4.75 changes include:
- Fyodor spent much of this summer scanning tens of millions of IPs on the Internet (plus collecting data contributed by some enterprises) to determine the most commonly open ports. Nmap now uses that empirical data to scan more effectively.
- Zenmap Topology and Aggregation features were added, as discussed in the next news item.
- Hundreds of OS detection signatures were added, bringing the total to 1,503.
- Seven new Nmap Scripting Engine (NSE) scripts were added. These automate routing AS number lookups, “Kaminsky” DNS bug vulnerability checking, brute force POP3 authentication cracking, SNMP querying and brute forcing, and whois lookups against target IP space. Many valuable libraries were added as well.
- Many performance improvements and bug fixes were implemented. In particular, Nmap now works again on Windows 2000.
Many of these changes were discussed in Fyodor's Black Hat and Defcon presentations. The audio and video has now been posted on the presentations page.
Download the source tarball or binaries for Linux, Windows, or Mac OS X from the Nmap download page. If you find any bugs, please report them.
Zenmap Gains Topology Maps and Aggregation Features
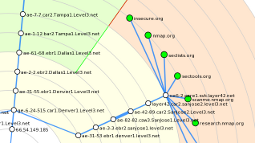
While Nmap stands for “Network Mapper”, it hasn't been able to actually draw you a map of the network—until now! The new Zenmap Network Topology feature provides an interactive, animated visualization of the hosts on a network and connections between them. The scan source is (initially) in the center, with other hosts on a series of concentric circles which represent the number of hops away they are from the souce. Nodes are connected by lines representing discovered paths between them. Read the full details (and oogle the pretty pictures) in our article on Surfing the Network Topology. Special thanks go to João Medeiros, David Fifield, and Vladimir Mitrovic for their tireless work in developing and integrating this new feature.
Another exciting new Zenmap feature is scan aggregation, which allows you to combine the results of many Nmap scans into one view. When one scan is finished, you may start another in the same window. Results of the new scan are seamlessly merged into one view.
You can try these and many other great features with the latest version of Zenmap, available from the Nmap download page.
Nmap Summer News Roundup
- Fyodor spoke in Las Vegas at the Black Hat Briefings and Defcon to discuss the results of large-scale Internet scans he has been conducting, and demonstrate how you can use the empirical data to make your scans (over the Internet or even internal) more efficient. He also showed off some new Nmap features which can help you bypass firewall restrictions, reduce scan times, and gather more information about remote hosts. The presentation video is now available on the presentations page.
- RSS feeds for mailing lists archived by SecLists.Org now sport message excerpts to make it easier to identify interesting messages.
- We now have a working search engine which covers all of our sites (Insecure.Org, Nmap.Org, SecLists.Org, and SecTools.Org. You can find the search bar on the left sidebar or bottom of our normal pages, or visit our search page directly.
- And for a bit of fun news, Nmap's movie stardom has grown with an appearance in its seventh movie!
Nmap Celebrates 10th Anniversary With Major Version 4.50 Release
After nearly two years of work since the 4.00 release, Insecure.Org is pleased to announce the immediate, free availability of the Nmap Security Scanner version 4.50 from https://nmap.org . Nmap was first released in 1997, so this release celebrates our 10th anniversary!
Major new features since 4.00 include the Zenmap cross-platform GUI, 2nd Generation OS Detection, the Nmap Scripting Engine, a rewritten host discovery system, performance optimization, advanced traceroute functionality, TCP and IP options support, and nearly 1,500 new version detection signatures. Dozens of other important changes—and future plans for Nmap—are listed in the release announcement. We recommend that all current Nmap users upgrade.
Update: Joe Barr at Linux.Com has written a great review of Nmap 4.50. In addition to testing the new features, he offers substantial background information on port scanning.
Nmap Featured in The Bourne Ultimatum
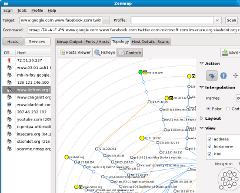
In The Bourne Ultimatum (IMDB), the CIA needs to hack the mail server of a newspaper (The Guardian UK) to read the email of a reporter they assassinated. So they turn to Nmap and its new official GUI Zenmap to hack the mail server! Nmap reports that the mail server is running SSH 3.9p1, Posfix smtpd, and a name server (presumably bind). They also make substantial use of Bash, the Bourne-again shell. Congratulations to Roger Chui for being the first to spot this. He also sent a scene transcript and the following HD screen shots (click for full resolution):
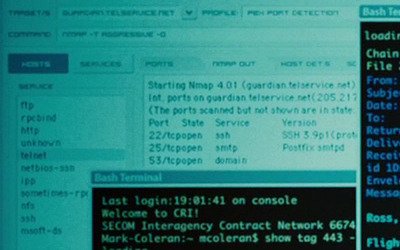

Other movies which have used Nmap include: Matrix Reloaded, Bourne Ultimatum, 13: Game of Death, Battle Royale, The Listening, and, uhh, HaXXXor: No Longer Floppy. Screens shots of Nmap in all of these movies are available on our new Nmap movies page. Nmap has become quite the movie star!
Introducing Zenmap, the Official Nmap GUI
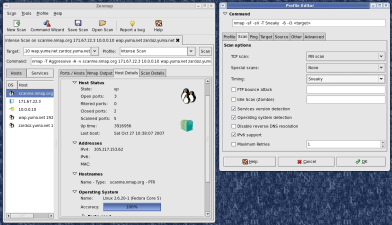
After more than two years of development (starting with a 2005 Google Summer of Code project), we have replaced the venerable but dated NmapFE with a new cross-platform GUI named Zenmap. It is cross platform (tested on Linux, Windows, Mac OS X) and supports all Nmap options. Its results viewer allows easier browsing, searching, sorting, and saving of Nmap results.
Zenmap will appear in the upcoming 4.50 release and is already available in the release candidate packages on the Nmap download page. Zenmap screenshots and documentation are available at https://nmap.org/zenmap.
Zenmap is still under active development, but was integrated early because it is already much more powerful than NmapFE. Development is coordinated on the nmap-dev mailing list.
Nmap Featured in Die Hard 4
Yippee Ki-Yay! In Die Hard 4: Live Free or Die Hard
(Wikipedia,
IMDB), Detective John McClane (Bruce Willis) is dispatched to retrieve hacker Matthew Farrell (Justin Long) because the FBI suspects him of breaching their computer systems. Later, Justin is enlisted to help thwart terrorist mastermind Thomas Gabrial's attempts at total World destruction. In this Scene, Farrell demonstrates his Nmap skills:

Thanks to Andrew Hake for catching the cameo and sending these HD screen shots.
See our Nmap movies page for many more movies featuring Nmap.
Top 100 Security Tools List Released
 After the tremendously successful 2000 and 2003 top security tools
surveys, we are pleased to release our 2006 results at a brand new
site: SecTools.Org. A record 3,243
Nmap users responded this year. Notable trends since 2003 include the
rise in exploitation frameworks such as Metasploit, Impact, and Canvas; the
increased popularity of wireless tools such as Kismet and Aircrack. 44 tools
are new to the list. Security practitioners are encouraged to read the list and investigate tools they
aren't familiar with. You may find the little gem that you never knew
you needed.
After the tremendously successful 2000 and 2003 top security tools
surveys, we are pleased to release our 2006 results at a brand new
site: SecTools.Org. A record 3,243
Nmap users responded this year. Notable trends since 2003 include the
rise in exploitation frameworks such as Metasploit, Impact, and Canvas; the
increased popularity of wireless tools such as Kismet and Aircrack. 44 tools
are new to the list. Security practitioners are encouraged to read the list and investigate tools they
aren't familiar with. You may find the little gem that you never knew
you needed.
English Sectools Coverage: Digg, Slashdot, About.Com, LinuxSecurity.Com, SANS ISC, TAOSecurity, del.icio.us, SecuriTeam, gHacks, iHacked
International: Menéame (Spanish), Kriptopolis (Spanish), ITPro Security (Japanese), Security.NL (Dutch), Todo-Linux (Spanish), CriticalSecurity (Lithuanian), Xakep (Russian)
SecLists.Org Back Up and Running
Our popular SecLists.Org public mailing list archive is back up and running after it was inexcusably shut down with no notice by our soon-to-be-former domain registrar GoDaddy at the behest of MySpace.Com. We believe web site content is the responsibility of the site owner (registrant) and (if that fails) hosting or bandwidth provider. If the whois contact data is valid, registrars shouldn't be involved without a court order.
News reports and discussion of the shutdown:
CNET News.Com |
Wired |
Wired #2 |
Slashdot |
Digg |
Politech |
Web Host Industry Reviews |
SecurityFocus |
Info World |
Domain Name Wire |
P2PNet |
SecurityPro News |
Digital MediaWire |
SecuriTeam |
Tech Dirt |
Mashable
Update: We have launched NoDaddy.Com to document GoDaddy's abuses of their registrar status.
Nmap 4.00 Released
After two years of work since the 3.50 release, Insecure.Org is pleased to announce the immediate, free availability of the Nmap Security Scanner version 4.00 from https://nmap.org .
Changes since version 3.50 include a rewritten (for speed and memory efficiency) port scanning engine, ARP scanning, a brand new man page and install guide, 'l33t ASCII art, runtime interaction, massive version detection improvements, MAC address spoofing, increased Windows performance, 500 new OS detection fingerprints, and completion time estimates. Dozens of other important changes -- and future plans for Nmap -- are listed in the release announcement.
Updates:
Fyodor has given a SecurityFocus interview on 4.00
More English coverage/reviews: Information Security Magazine, Slashdot, Linux Weekly News (LWN), Digg, SANS ISC, OSNews, AllYourTech.Com, LinuxSecurity.Com
International coverage: Heise (German), LinuxFR (French), OpenNET (Russian), derStandard (Austrian), Golem.de (German), Hacking.PL (Polish), WinFuture (German), Kriptopolis (Spanish), Security.NL (Dutch), Tweakers.Net (Dutch), Xakep (Russian)
Security List Archive Updated
RSS feeds have been added to all security mailing lists archived at SecLists.Org, making it even easier to keep up with the latest news from Nmap-Hackers, Nmap-Dev, Bugtraq, and all of the others. We have also added Dailydave, a highly technical discussion list covers vulnerability research, exploit development, and security events/gossip (with many smart people participating).
NSA Loads Nmap Release Status for President Bush Visit
US President George W. Bush visited the NSA headquarters at Fort Meade in January 2006. A wall-sized status screen in the background displays the latest versions of Nmap and some of our other favorite open source tools. Pictures were printed in the February 6, 2006 edition of Newsweek (article) and the Jan 27 Washington Post (article). The page on the screen is the Talisker Radar. We don't like the NSA tracking our phone calls and email, but they may track Nmap releases all they want.
Loading an external web site on their giant screen was risky. Imagine if this happened (thanks php0t)!
Meanwhile, Nmap makes an appearance at Walmart with the Nmap hacking chair
New Nmap Man Page
We are proud to announce that the Nmap man page has been completely rewritten. It is more comprehensive (double the length) and much better organized than the previous one. It is meant to serve as a quick-reference to virtually all Nmap command-line arguments, but you can learn even more about Nmap by reading it straight through. The 18 sections include Brief Options Summary, Firewall/IDS Evasion and Spoofing, Timing and Performance, Port Scanning Techniques, Usage Examples , and much more. It even documents some cool features that are slated for release in the next Nmap version (runtime interaction and parallel DNS resolution).
The new man page is best read in HTML format, though you can alternatively download the Nroff nmap.1 to install on your system.
We have issued a call for translations of the reference guide, and 29 languages are in progress. See the new documentation page to volunteer or read a translation.
Hacker Fiction Books Published
 | Fyodor has co-authored a novel on hacking, along with FX, Joe Grand, Kevin Mitnick, Ryan Russell, Jay Beale, and several others. Their individual stories combine to describe a massive electronic financial heist. While the work is fiction, hacks are described in depth using real technology such as Nmap, Hping2, OpenSSL, etc. Stealing the Network: How to Own a Continent can be purchased at Amazon (save $17), and your can read Fyodor's chapter online for free. STC was a best-seller, ranking for a while as the second-highest selling computer book on Amazon. |
 | Update: Syngress has released a sequel: Stealing the Network: How to Own an Identity. They have generously allowed Fyodor to post his favorite chapter for free. So enjoy Bl@ckTo\/\/3r, by Nmap contributor Brian Hatch. It is full of wry humor and creative security conundrums to keep the experts entertained, while it also offers security lessons on the finer points of SSH, SSL, and X Windows authentication and encryption. |
Nmap Gains Advanced Version Detection
After several months of intense private development, we are pleased to release Nmap 3.45, including an advanced version detection system. Now instead
of using a simple nmap-services table lookup to determine a port's
likely purpose, Nmap will (if asked) interrogate that TCP or UDP
port to determine what service is really listening. In many cases it
can determine the application name and version number as well.
Obstacles like SSL encryption and Sun RPC are no threat, as Nmap can
connect using OpenSSL (if available) as well as utilizing Nmap's RPC
bruteforcer. IPv6 is also supported. You can read our new version detection paper for the
details and examples, or just download the latest version and try it
out here. Simply add "-sV" to your normal scan
command-line options.
News articles covering Nmap version detection: Slashdot, Hacking Linux Exposed, Security Wire Digest.
Nmap Featured in The Matrix Reloaded
We have all seen many movies like Hackers which pass off
ridiculous 3D animated eye-candy scenes as hacking. So I was
shocked to find that Trinity does it properly in The Matrix Reloaded [Under $6 at Amazon].
She whips out Nmap version
2.54BETA25, uses
it to find a vulnerable SSH server, and then proceeds to exploit it
using the SSH1
CRC32 exploit from 2001.
Shame on them for being vulnerable (timing notes). Congratulations to everyone who has helped
make Nmap successful! Click on these thumbnails for higher resolution or view more pictures
here.

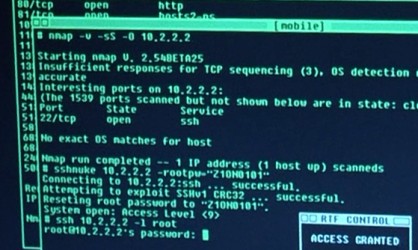
Updates:
- News articles about the Nmap cameo: BBC, Slashdot, SecurityFocus, Silicon.Com, CNET
- JWZ has added this cracking scene as an XScreenSaver 4.10 Easter Egg - run 'xmatrix -small -crack'.
- Dave from Lab6 notifies me that Nmap source code is displayed in Battle Royale: [Screen1] [Screen2] [Trivia]
- Several people have submitted matrix-themed banners to the propaganda gallery. Feel free to use any of these to link to Insecure.org - we appreciate it!
- The UK's Scotland Yard Computer Crime Unit and the British Computer Society have put out a joint warning that "Viewers of the new box office blockbuster 'Matrix Reloaded' should not be tempted to emulate the realistic depiction of computer hacking." Kids - don't try this at home!